How to integrate OAM & OAAM 11g R2 PS2 (11.1.2.2.0)
Oracle Access Manager & Oracle Adaptive Access Manager 11g R2 PS2(11.1.2.2.0) Integration
Environment:
-- Oracle Access Manager 11g R2 PS2(11.1.2.2.0)
-- Oracle Adaptive Access Manager 11g R2 PS2(11.1.2.2.0)
-- Oracle Database 11g
-- Oracle WebLogic Server 10.3.6
-- Oracle Enterprise Linux 64-bit
-- Oracle Repository Creation Utility 11g R2 PS2(11.1.2.2.0)
-- Oracle HTTP Server 11g R1
-- OAM WebGate for OHS webserver 11.1.1.7.0
-- OAM user store is Weblogic embedded LDAP
Steps:
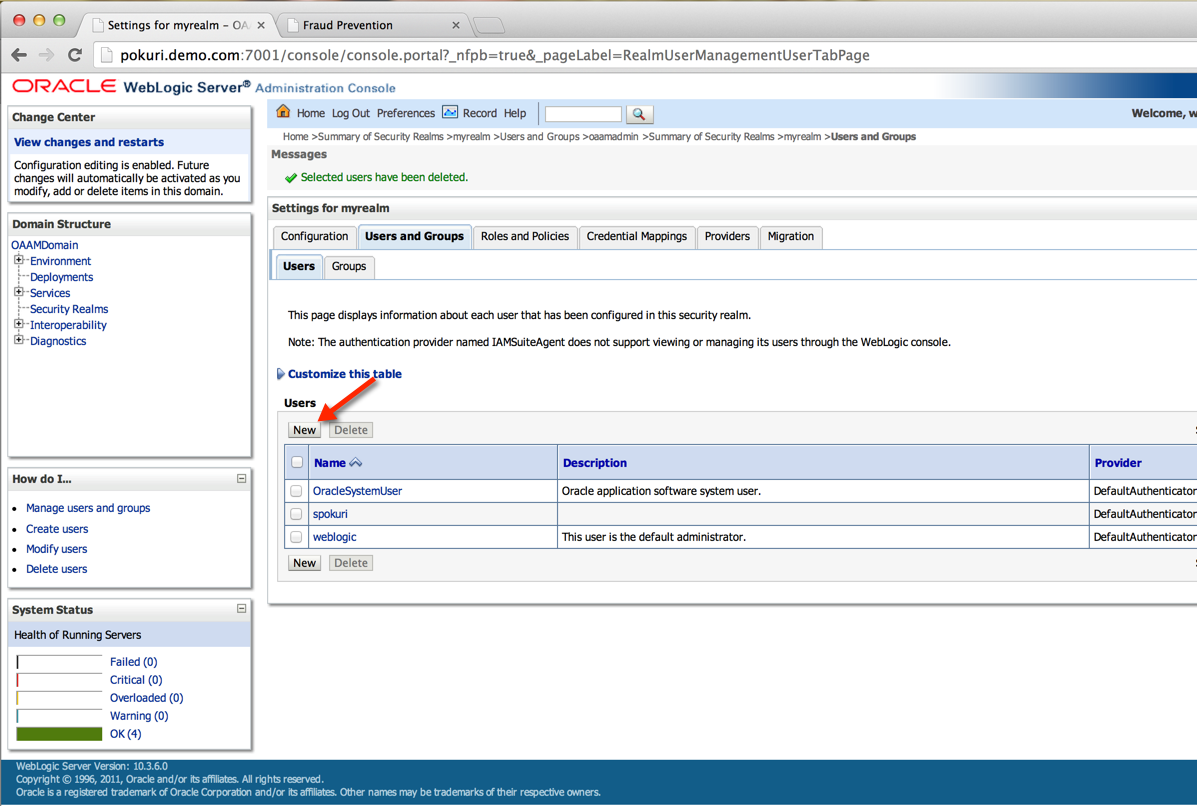
-- Login to Weblogic Administration console and create "oaamadmin" user and assign all the OAAM admin privileges.
-- Login to OAAM Admin console and add property as shown in the below screen shot
-- Follow below screen shots to create TAP key Store.
-- Assign a password for IAMSuiteAgent in OAM Admin console and update the same in Weblogic Administration console Security Realm>> IAMSuite Agent provider
-- Restart all OAM and OAAM admin & managed servers.
-- Update TAP Scheme challenge parameters as shown in the below screen shots.
-- Setup OAM Integration with OAAM.
-- Update the OAM, OAAM details in oaam_cli.properties file as shown in the below screen shot.
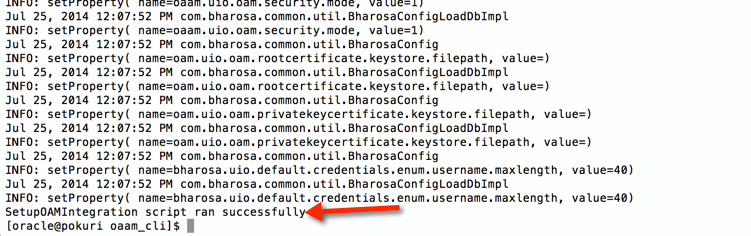
-- Set ORACLE_MW_HOME environment variable and execute setupOAMTapIntegration.sh as shown in the below screen shots
-- Enter "oaamadmin" user(which we created in the first step) and enter the password followed by OAAM database credentials and TAP keystore password.
-- Verify oaam.uio.security.mode property value set to 1 in OAAM Admin console properties.
Testing:
Change any existing protected resource Authentication Schema from "LDAP Scheme" to "TAPScheme" and try to access the protected resource and try login with a valid user in the directory server.
-- Successfully logged in with OAAM security profile setup.
Hope this helps.
Thanks
Siva Pokuri.











































Hi Siva,
ReplyDeleteIs there any way to associate a custom OAAM pre or post auth policy with a specific resource.
We have TAP integration working. Now what we want to do is to force the user to answer one of their KBA questions every time they access this TAP scheme protected URL and this URL alone. The key word is 'everytime'. By default OAAM will fingerprint the device and only if the risk score is higher than the threshold, will it challenge the user. This will typically only happen when the user is accessing the TAP URL for a second time from a different device/browser.
If the user was accessing another URL protected by the TAP scheme, then we do not want the user to be challenged. So how does one associate a OAAM policy with a specific URL/resource that is protected by the TAP scheme in OAM?
Thanks
Aspi Engineer
Hi,
ReplyDeleteYou can use OAAM SOAP API's in your application to trigger challenge in OAAM when you navigate to that URL in application.
Mail me at sivakrishna.pokuri@gmail.com if any questions.
-- Siva Pokuri.